
1. Overview
Over the years, the company has focused on the development of equipment and system applications in multi-link intelligent networking and multi-medium distributed storage technologies, revolving around its independently developed?Data Fragmentation?Technology. This includes:
(1) Data Fragmentation?Technology: This technology uses a triad approach of “encryption algorithm + granularization algorithm + physical separation” to protect business data, providing more stable and reliable computational security for business data.
(2) Multi-Link Intelligent Networking Technology: This technology utilizes multi-system, multi-channel communication systems already established by users or the state to achieve multi-channel parallel distribution of data particles, fully leveraging the advantages of multi-channel integration to improve data transmission efficiency.
(3) Multi-Medium Distributed Storage Technology: This involves storing granulated data across multiple storage media, with each medium containing incomplete data. By placing these media in different locations, the security of user data applications is ensured.
2. Domestic and International Development
Currently, in the fields of information security communication and secure storage in China, data security is commonly achieved through computational security and optimal channel link selection.
In terms of secure communication, to ensure reliable transmission, communication systems are generally equipped with multiple channels, including fiber optics, duplicated lines, satellites, Beidou short messages, broadband wireless self-organizing networks, LTE private networks, public 3G/4G networks, etc. Communication control devices select channels to use in the order of “primary, backup, emergency” based on usage scenarios, requirements, and channel quality, with secure transmission generally solved through channel encryption. To expand communication rates, bundling multiple 3G/4G channels or multiple fiber optic E1 channels to transmit high-definition video and other high-speed data also has certain market applications.
In terms of secure storage, data is generally encrypted and stored on hard drives or optical discs, or the storage medium containing unencrypted data is placed in a secure environment to ensure the storage safety of the data.
In the field of information encryption, with the rapid development of computational capabilities such as quantum computing, cloud computing, and supercomputers, the traditional data encryption regime is facing significant challenges and substantial threats. The security assurance provided by computational security can only be enhanced through measures such as algorithm optimization and expansion of the cryptographic space. There is an urgent need to explore and research new methods and means to enhance security.
3. Technology Principle and Application Efficacy
3.1 Technology Principle
(1) Data Granularization Technology
Data granularization technology shatters plaintext business data into data fragments with computational security and information-theoretic security characteristics through random permutation and data fragmentation. The process of granularization is as shown in the diagram:
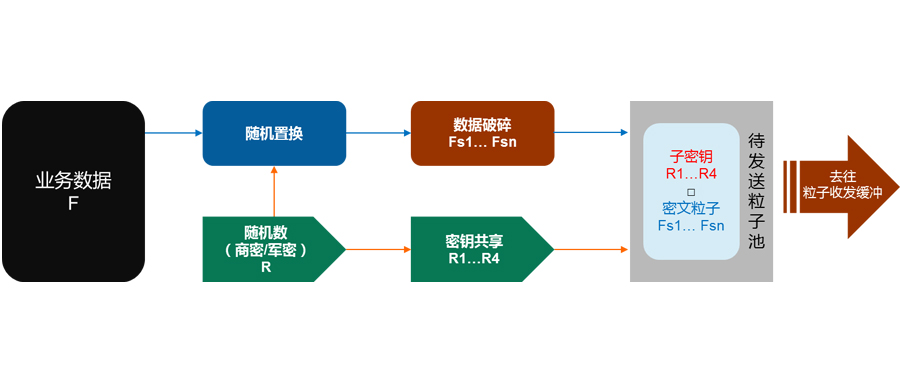
(2) Multi-Link Intelligent Networking Technology
Multi-link intelligent networking technology is the process of intelligently sensing link status, automatically selecting available links, fusing multiple available links into a virtual link, and achieving multi-channel concurrent transmission within the virtual link. This technology uses data particles provided by the granularization algorithm as input, consisting of stages such as transparent proxy, multi-channel connection management, and multi-channel parallel distribution as shown in the diagram:
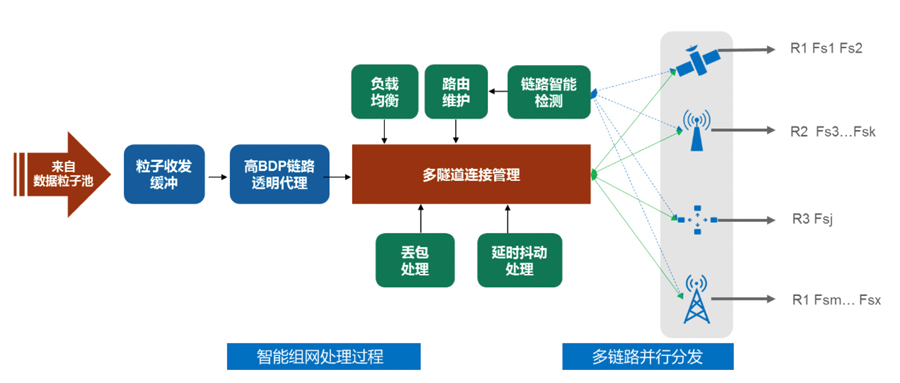
(3) Multi-Medium Distributed Storage Technology
Multi-medium distributed storage technology draws inspiration from modern “shredders” and ancient “tiger tally seals,” shattering and granularizing data and automatically distributing it to several different media, such as multiple hard drives or optical discs placed in different locations or carried by multiple people. This elevates static data security from a two-dimensional plane of “algorithm – key” to a three-dimensional structure of “algorithm – key – data fragment,” ensuring the safe and reliable storage of data.
3.2 Application Efficacy
(1) The combination of information-theoretic security and computational security effectively enhances information security and anti-interception capability.
The multi-link intelligent networking and multi-medium distributed storage technology based on data granularization elevate the data security of information storage and transmission from computational security to a level combining data security with information-theoretic security. Multi-link concurrent transmission / distributed storage can achieve a security enhancement millions of times higher than traditional packet encryption when data particles are partially intercepted. Even if data particles are completely intercepted and reassembled, their security is equivalent to traditional packet encryption, significantly increasing the difficulty of intercepting and decrypting business data, effectively enhancing information security.
Additionally, multi-link granularization intelligent networking technology constructs a secure virtual private network with multiple nodes connected through different channels. All business systems are invisible and unreachable to the physical communication link, turning the business system network into a hidden network behind the virtual private network, providing a secure access barrier for business systems.
(2) Through multi-link integration and intelligent networking, effectively improve communication efficacy and environmental adaptability.
Through multi-link aggregation, the characteristics of multiple channels of existing communication systems can be fully utilized, improving communication efficacy and avoiding the waste of communication resources. Using link detection perception and load balancing, without manual intervention, automatically adjusts to adapt to the transmission conditions of each channel, ensuring real-time, efficient, and uninterrupted transmission of information under complex electromagnetic countermeasure conditions.
In terms of link fusion efficiency, the virtual link bandwidth generated by multi-link granularization intelligent networking technology is related to the number of physical channels. Through tests on 3G/4G links, when each link’s bandwidth is counted as 1, the bandwidth of the virtual link after merging two physical channels is 1.7 ~ 1.8; after merging three physical channels, it is 2.4 ~ 2.5.
Unlike transparent transmission, all protocols incur link overhead during link transmission, requiring the addition of protocol fields and error correction redundant coding on normal business data. Additionally, key sharing overhead is generated during the encryption and decryption process. The total link overhead generated by multi-link granularization intelligent networking technology in the multi-channel fusion process does not exceed 10%, including data expansion overhead
and intelligent networking overhead. Among them, data expansion overhead is only generated during key sharing processing, with an expansion overhead of less than 4.68%, which is essentially the same as the overhead brought by traditional encryption; intelligent networking overhead is generated during multi-channel parallel distribution, with a calculated networking overhead of about 5.21%, slightly higher than the traditional TCP/IP protocol overhead.
(3) Fully utilize civilian mobile communication resources to achieve long-range mobile secure communication applications.
Utilizing the wide-area coverage of the civilian mobile communication network within the country, by aggregating multiple 3G/4G/5G routes through granularization and shattering, sensitive information’s security application problems are solved while realizing large-span mobile applications for users, solving “communication on the move” support, in conjunction with other communication methods, ensuring “always available, always usable” communication, ensuring real-time and uninterrupted communication.
Additionally, utilizing the wide coverage, high rate, and large capacity of civilian resources, voice dispatch, high-speed data, high-definition video, navigation and positioning, and other multi-service direct access applications can be realized. Traditional wired communication terminals (video phones, automatic phones, fax telegrams, etc.) can also be expanded through civilian wireless channels using wired/wireless conversion, protocol adaptation, etc., solving the emergency use of mobile or temporary tasks.